Chrome 内核浏览器紧急发布了高危漏洞通知。
谷歌发出紧急警告,要求立即更新浏览器,以避免 0day 漏洞的攻击。这种 0day 漏洞已经在互联网攻击中被发现,影响 Chrome 浏览器,攻击者可以远程控制用户的系统。这个漏洞被分类为高危安全漏洞,影响Windows、macOS 和 Linux 系统上所有版本的 Chrome 内核浏览器。包括但不限于 Chrome、Microsoft Edge、Brave Browser、Arc Browser 等。
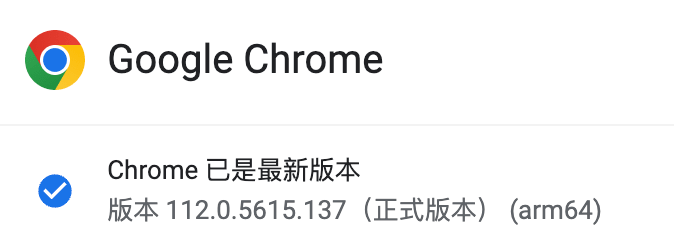
稳定版的 Windows 版本已更新到 112.0.5615.137/138,Mac 版本已更新到 112.0.5615.137,Linux 版本已更新到 112.0.5615.165。请尽快更新浏览器版本。
以下是 CVE 漏洞编号
[$8000][1429197] High CVE-2023-2133: Out of bounds memory access in Service Worker API. Reported by Rong Jian of VRI on 2023-03-30
[$8000][1429201] High CVE-2023-2134: Out of bounds memory access in Service Worker API. Reported by Rong Jian of VRI on 2023-03-30
[$3000][1424337] High CVE-2023-2135: Use after free in DevTools. Reported by Cassidy Kim(@cassidy6564) on 2023-03-14
[$NA][1432603] High CVE-2023-2136: Integer overflow in Skia. Reported by Clément Lecigne of Google's Threat Analysis Group on 2023-04-12
[$1000][1430644] Medium CVE-2023-2137: Heap buffer overflow in sqlite. Reported by Nan Wang(@eternalsakura13) and Guang Gong of 360 Vulnerability Research Institute on 2023-04-05
漏洞披露的细节请参考 issue




